Over the past couple of years in Scambaiting a trend has occurred were people have deleted files and destroying computers. Typically, this is done by people who don’t know what they’re doing and just want to either troll the scammer or help but I am here to say, it doesn’t do much damage and even in cases it does, it isn’t the best option.
Now, I have made a thread like this before but it isn’t the best laid out etc. so I thought I’d make a new one.
Intro
So lets get started:
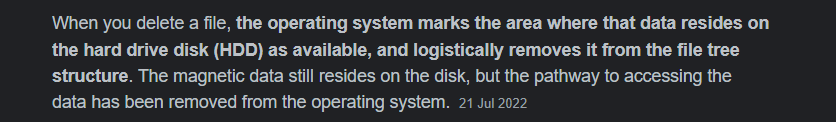
A while ago I was dealing with a scammer and noticed he had a program on his computer to recover deleted files x.com and how it works is files aren’t actually deleted
Is this illegal?
In the US: https://www.cga.ct.gov/2012/rpt/2012-r-0254.htm
In the UK:
The Act also makes it an offence to make, adapt, supply or obtain articles for use in unlawfully gaining access to computer material or impairing the operation of a computer.
Access is defined in the Act as:
altering or erasing the computer programme or data
copying or moving the programme or data. (Department of Health, 2015)
Department of Health (2015). The Computer Misuse Act 1990 | Department of Health. [online] Department of Heath. Available at: The Computer Misuse Act 1990 | Department of Health [Accessed 1 Dec. 2022]. The Act also makes it an offence to make, adapt, supply or obtain articles for use in unlawfully gaining access to computer material or impairing the operation of a computer.
Access is defined in the Act as:
altering or erasing the computer programme or data
copying or moving the programme or data.
[center][size=4]Why deleting files is pointless[/size][/center]
Now, you may be thinking scammers are too stupid to recover files this way and that is false. Now, most scammers probably don’t do this when their files get deleted, most scammers aren’t bothered and can just move on as the usual files like leads list and victim data isn’t that important as the victims numbers will be in their VOIP logs and in some cases sent to a higher or the boss but either way they will get new victims in the future so loosing some victims is not that big of a deal. Same with lead lists and if its saved they probably already dialled that leads list anyways making it used and not important to the scammers.
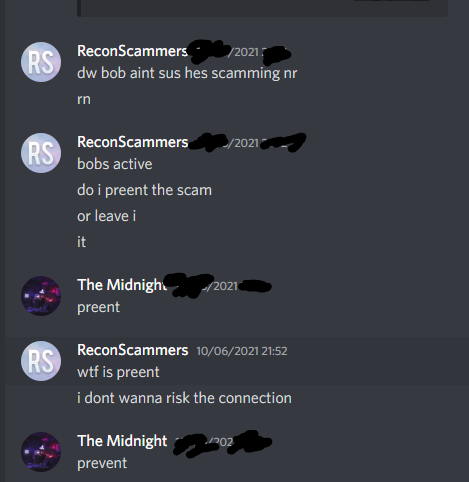
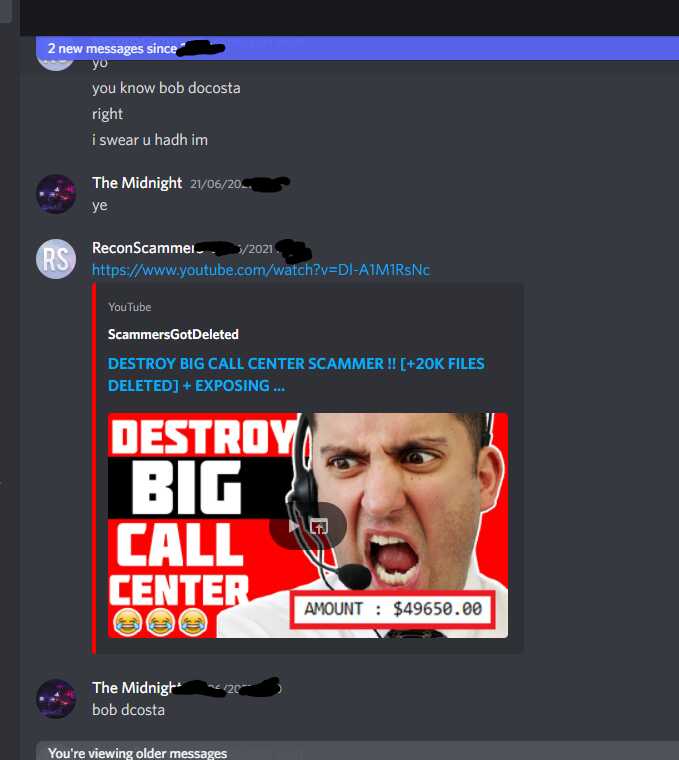
They can just setup again easily making it pointless. If you look at people like Jim Browning they have gained access to CCTV and a raid www.youtube.com/watch?v=P6dhteJIY48 and another baiters raid https://www.youtube.com/watch?v=qmd_gIFTLTo, notice how they all have cameras, that seems to be one of the keys for these raids, just downloading files won’t cause a raid looking at these videos. Destroying scammers computers destroys that opportunity and it removes evidence for the police. It can also destroy other scam baiters operations for example https://www.youtube.com/watch?v=Dl-A1M1RsNc while you should not send hate to this person, my friend @TheMidnight aka Midnight Scambaits https://www.youtube.com/@MidnightSB was watching this computer called Bob Docsta (this happened in 2021) and ended up loosing the connection because of this, other people I work with have had other run in’s with baiters who have deleted files.
Me and Midnight were watching this scammer and attempting to save victims in the process, this stopped that.
Same with running viruses/malware such as ransomware or memz etc. that is destructive or otherwise would alert the scammer that they have been hacked (different from what someone like Jim Browning does), while I don’t do it, it all depends on the situation, if your not effecting other baiters and you have monitored for a while and have good information then you do you, I have friends who do this once they’ve watched for a while if they plan on making a video out of it. I don’t completely agree with this, I know that they know they aren’t being stupid while doing it.
All this really does is teach them that they are vulnerable to this and most I have seen end up realising its done and uninstalling any software that could make them vulnerable to this which prevents this method being done in the future by more experienced baiters like Jim Browning or Scambaiter etc.
Why deleting files on its own doesn’t save victims
On the topic of victims, deleting files doesn’t save victims either. For some it may cause a small down time but any victims they had actually won’t be saved. Here are the reasons for this: the victim will still have the remote software on their computer, if its something like ConnectWise/ScreenConnect then the scammer will still have access to the victims computer and will be able to monitor, the victim has not been warned of the scam and has not been given a resource on scams and will most likely be victimised again in the future, their information is not secure the scammer could have their SSN or banking information; that information needs securing and their passwords changed and help with trying to recover the fund. Deleting files just isn’t enough in that situation. Now, you may be thinking ‘but the scammer still has the victim information, they will recontact and scam them’ and what I can say is they have a resource on scams, a way to contact back for help then this shouldn’t be too huge of an issue as it will prepare them for scams, plus it’s better than making the scammer aware he’s been accessed and research and learn how to prevent it in the future or realise.
What I suggest people do
I do not suggest people access scammers computers due to the fact it is illegal and the fact new baiters won’t know what to do. It could turn into giving victims back advice or nuking the computer by not knowing what to do. I suggest leaving this stuff to people like; Jim Browning, Scammer Payback, Scambaiter, NanoBaiter, Midnight Scambaits, HowToDelete Took me a while to learn the proper way to do things, before then I would either screw things up or miss important things. Caused issues and learnt. You don’t want to be a problem in this community, you wanna have people to guide you but not a lot of people would do that with random people as you need trust for this side of scambaiting as you see victim information, scammers information such as ID cards that a bad actor could easily mis-use, won’t mention names but I know of a Scambaiter (who me and the people I work with was told he was reported to the police by someone with his actual information) who was stealing from victims using information he got off the scammers computer. This is one of the main reasons I don’t teach people what I and others like Jim do.
Ending
I know we all have our own methods but as someone who knows about this topic, it really isn’t the right way. It gets actual baiters mad who put time and effort into finding out who these scammers are and saving victims etc. Plus, the baiters who do this for the most part I have seen just be immature in baits, curse a lot at the scammers and reveal treating it more as a game than being professional. While, you should have fun while baiting you shouldn’t be like ‘oh my I deleted your files’ and then make them aware you did it and teach them. If your going to do something where you have the up and up on a scammer such as gain wire information etc. why would you reveal and make it so they won’t give up that stuff in the future, I think it’s dumb.
TL;DR deleting files is illegal and just makes the scammers aware, they can restore from backups or recover deleted files and it could effect other baiters work and theirs a lot more you can do.