Hello I am back with a couple of new scripts (Thanks ChatGPT) for these, These scripts are intended to map out stupidity of scammers. Since with a I do believe Jim Browning video? We seen scammers just drag and drop files from one AWS bucket to another to avoid a scam report? This is essentially able to counter lazy scammers by building a list of their webpage hashes and allowing you to use shodan to monitor them along with monitoring their SSL Certs as well.
The first script is known as MMH3.py this can be used to calculate MMH3 Hashes of .html & .ico files. This project was for NFTs & Crypto (Hence the ability to clone github repos) but has since branched out to other things.
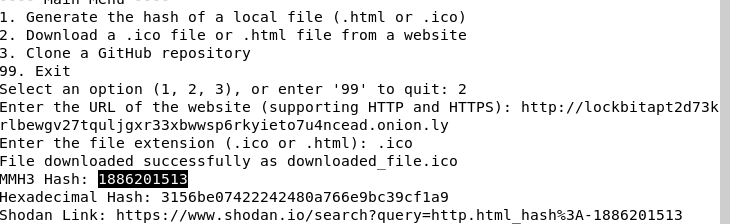
There is a problem with .ico files instead of giving you a direct shodan link it prints one for .html. I Plan to fix this soon but the opertor on shodan is hash: and not http.html_hash:
Also it should be noted that you are required to have an account on shodan or else search features fail to work. I Have paid the 1-time payment for the additional pages & Larger daily search amount.
The second script is known as SSL-gen.py this will grab the HASH of a SSL Cert of any website and can be used on Censys by creating an account and using the subdomain search. (search.censys.io) once logged in you’ll see a “hosts” drop down click certificates (Legacy) do not use 2.0 it’s annoying. Once here you can use parsed.fingerprint_sha1: or parsed.fingerprint_md5 Also supports SHA-256 just changed sha1 to sha256
This can be used to find websites along with websites sharing the same SSL, Unlike a MMH3 Hash SSLs don’t change when the page is updated and could open the doors to leaking their IPs, Location and etc because a lotta morons just slap their SSL around and it causes issues.
YES, THE SCRIPT DOES SUPPORT TOR HIDDEN SERVICES THROUGH A SHITTY PROXY SERVICE
change .onion to .onion.ly and it’ll do what you want.
Known annoying things: If you select option 2 in MMH3.py it will force you to add http:// or https:// failure will cause a fatal error.
We plan to further make shit even more quick, easy and lazy. Automation at it’s finest.
Example of Lockbit Ransomware’s blog having it’s fav.ico MMH3 Hash genned and the damn shodan failure
Why did we make this? Simply because we see a lot of Malware C2s who use the same dumbass panel and do not change jack shit so, we made it to quickly gen a hash (Since there’s lack of a brain-dead level hash gen) and allow anyone to quickly query shodan for potential C2 Panels or OPSEC Fails.
This runs on python3 I’m sure you can use google or youtube to figure out how to install and for windows users? Just download a virtual machine and use linux for the love of god. If you don’t add pip & python to path it’s annoying to figure shit out due to the 98+ threads that do not assist you