Hello guys, I created a python script that can be used to target forms in phishing websites. The concept behind it is to make it harder for scammers and hackers to exploit the data collected by these fraudulent forms. This can especially be useful if a phishing site doesn’t include a phone number.
It works by submitting false data to the forms. However this does require the user to look at the form in raw HTML and get the input tags name and modify the payload inside the script. Because of this, I only recommend it be used by people (will be adding a configuration fill in the future).
Usage example
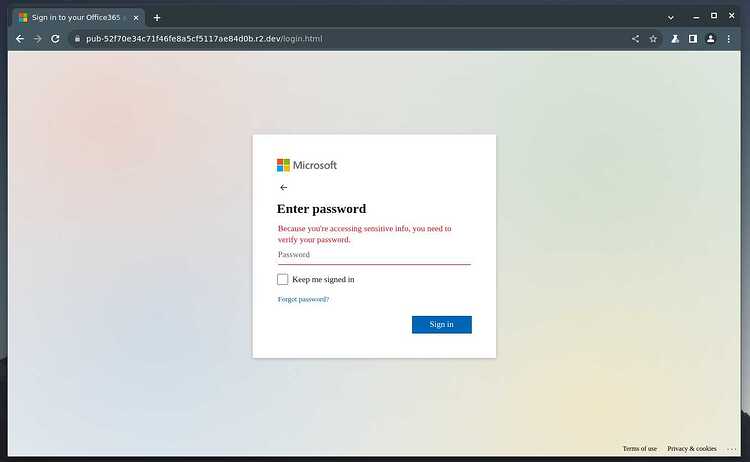
Lets say we found a phishing website, it doesn’t include a phone number so normal scam baiting tactics might not work out, well I found just that website (http://pub-52f70e34c71f46fe8a5cf5117ae84d0b.r2[.]dev/login.html) . That site looks like this.
we can see that the site is a fake Microsoft site. (hint, the background gradient is a little dull compared to the real) . So lets get the input name, we can do this with the inspector element.
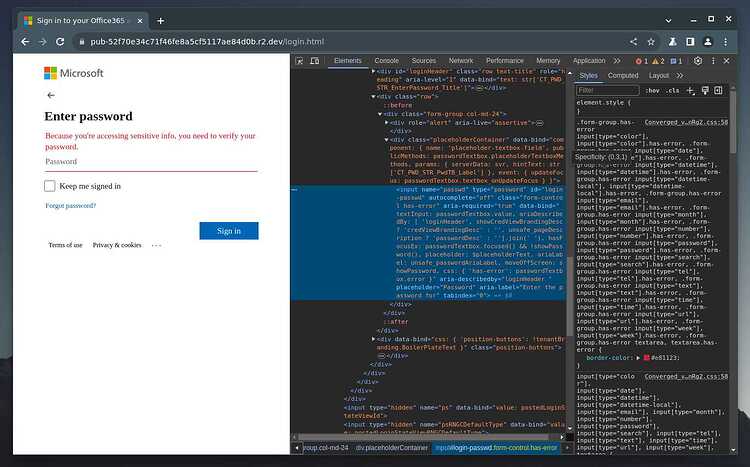
using the element selector (top left icon with arrow). we select the input field an we can see that we can jump to the input element. we want to look for the name=“” attribute which has a value of “passwd”. lets modify our code to take advantage of this.
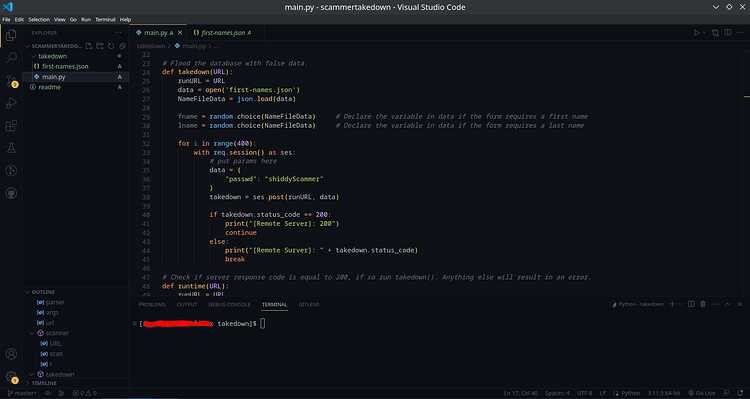
on line 35 (in v0.1.0) is that data variable, we can see I already have the the variable configured for this site.
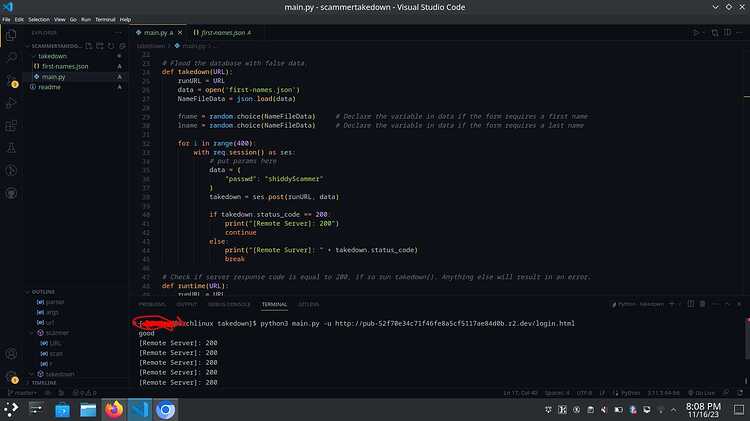
and all we need to do to launch is type
python3 main.py -u your-target-url
as you see we get a response code of 200, this means OK, so its working just the way we want it to.
Let me know what you thought of this, and what you think should be added.
and of course, here is the GitHub link: GitHub - tester1901/Scammer-takedown: A scambaiting tool for flooding a scammers database with false data.