-
polyfill.io, a popular JavaScript library service, can no longer be trusted and should be removed from websites according to Cloudflare. Multiple reports, corroborated with data seen by Cloudflare’s own client-side security system, Page Shield, have shown that the polyfill service was being used, and could be used again, to inject malicious JavaScript code into users’ browsers. This is a real threat to the Internet at large given the popularity of this library. The original report indicates that malicious code was injected that, under certain circumstances, would redirect users to betting sites. It was doing this by loading additional JavaScript that would perform the redirect, under a set of additional domains which can be considered Indicators of Compromise (IoCs):
https://www.googie-anaiytics.com/analytics.js
https://www.googie-anaiytics.com/html/checkcachehw.js
https://www.googie-anaiytics.com/gtags.js
https://www.googie-anaiytics.com/keywords/vn-keyword.json
https://www.googie-anaiytics.com/webs-1.0.1.js
https://www.googie-anaiytics.com/analytics.js
https://www.googie-anaiytics.com/webs-1.0.2.js
https://www.googie-anaiytics.com/ga.js
https://www.googie-anaiytics.com/web-1.0.1.js
https://www.googie-anaiytics.com/web.js
https://www.googie-anaiytics.com/collect.js
https://kuurza.com/redirect?from=bitget
(note the intentional misspelling of Google Analytics) -
Cloudflare, over the last 24 hours, have released an automatic JavaScript URL rewriting service that will rewrite any link to polyfill.io found in a website proxied by them to a link to their mirror under cdnjs. This will avoid breaking site functionality while mitigating the risk of a supply chain attack. Any website on the free plan has this feature automatically activated now. Websites on any paid plan can turn on this feature with a single click. You can find this new feature under Security ⇒ Settings on any zone using Cloudflare.
-
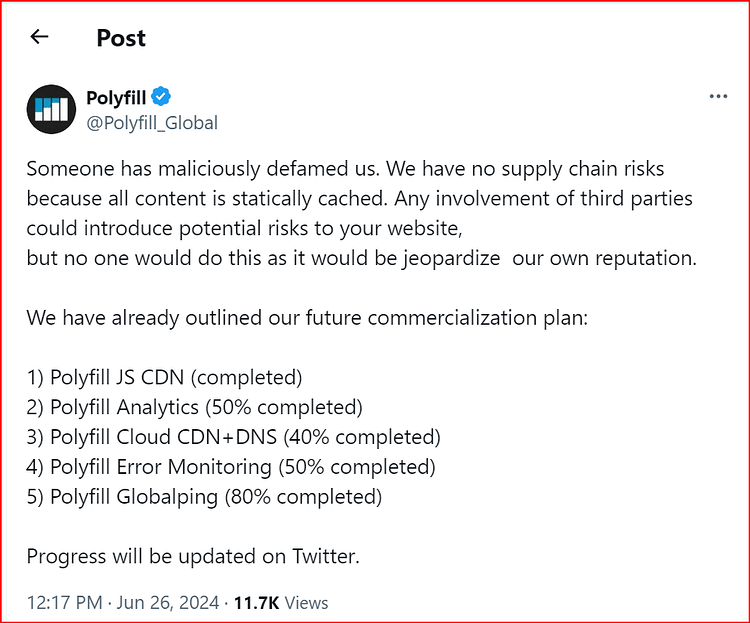
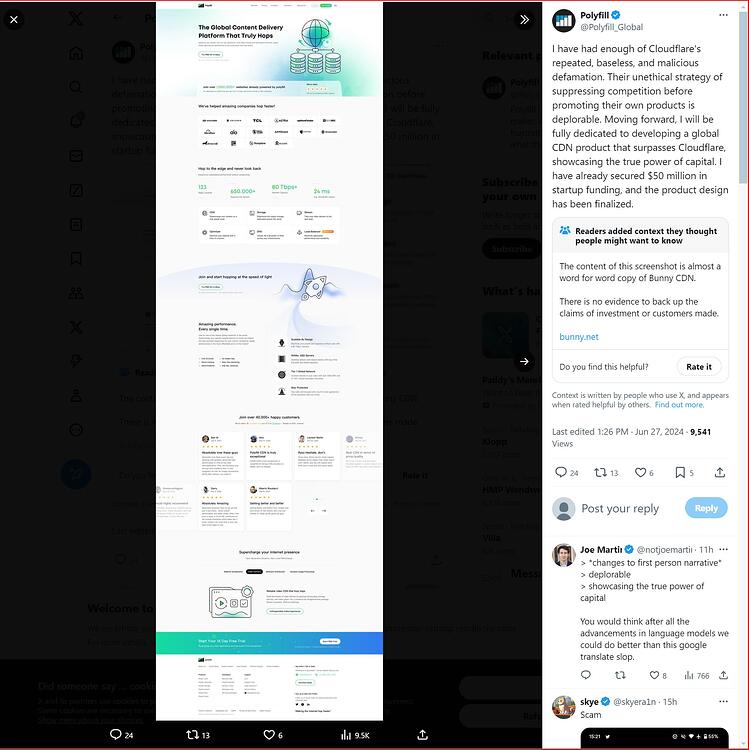
Contrary to what is stated on the polyfill.io website, Cloudflare has never recommended the polyfill.io service or authorized their use of Cloudflare’s name on their website. Cloudflare have asked them to remove the false statement, and they have, so far, ignored their requests. This is yet another warning sign that they cannot be trusted. Search your code repositories for instances of polyfill.io and replace it with cdnjs.cloudflare.com/polyfill/ (Cloudflare’s mirror). This is a non-breaking change as the two URLs will serve the same polyfill content. All website owners, regardless of the website using Cloudflare, should do this now. Cloudflare also say they have taken the exceptional step of using their ability to modify HTML on the fly to replace references to the polyfill.io CDN in their customers’ websites with links to their own, safe, mirror - The same one that was created back in February, of course.
-
If you are using Cloudflare, you can remove polyfill.io with a single click on the Cloudflare dashboard by heading over to your zone ⇒ Security ⇒ Settings. If you are a free customer, the rewrite is automatically active. The underlying bundle links you should use are: For minified: https://cdnjs.cloudflare.com/polyfill/v3/polyfill.min.js
For unminified: https://cdnjs.cloudflare.com/polyfill/v3/polyfill.js → Doing this ensures your website is no longer relying on polyfill.io. -
Back in February, the domain polyfill.io, which hosts a popular JavaScript library, was sold to a new owner: Funnull, a relatively unknown company. The new owner was unknown in the industry and did not have a track record of trust to administer a project such as polyfill.io. The concern, highlighted even by the original author, was that if they were to abuse polyfill.io by injecting additional code to the library, it could cause far-reaching security problems on the Internet affecting several hundreds of thousands websites. Or it could be used to perform a targeted supply-chain attack against specific websites. Unfortunately, that worry came true on June 25, 2024, as the polyfill.io service was being used to inject nefarious code that, under certain circumstances, redirected users to other websites.
-
In the meantime, additional threat feed providers have also taken the decision to flag the domain as malicious. Cloudflare say they have not outright blocked the domain through any of the mechanisms they presently have because they are concerned it could cause widespread web outages given how broadly polyfill.io is used with some estimates indicating usage on nearly 4% of all websites.
-
Page Shield, Cloudflare’s client side security solution, is available on all paid plans. When turned on, it collects information about JavaScript files loaded by end user browsers accessing (your) website. By then looking at the database of detected JavaScript files, they immediately found matches with the IoCs provided above starting as far back as 2024-06-08 15:23:51 (first seen timestamp on Page Shield detected JavaScript file). This was a clear indication that malicious activity was active and associated with polyfill.io.
-
To achieve performant HTML rewriting, Cloudflare needs to make blazing-fast HTML alterations as responses stream through Cloudflare’s network. This has been made possible by leveraging ROFL (Response Overseer for FL). ROFL powers various Cloudflare products that need to alter HTML as it streams, such as Cloudflare Fonts, Email Obfuscation and Rocket Loader. ROFL is developed entirely in Rust. The memory-safety features of Rust are indispensable for ensuring protection against memory leaks while processing a staggering volume of requests, measuring in the millions per second. Rust’s compiled nature allows Cloudflare to finely optimize their code for specific hardware configurations, delivering performance gains compared to interpreted languages. The performance of ROFL allows Cloudflare to rewrite HTML on-the-fly and modify the polyfill.io links quickly, safely, and efficiently. This speed helps Cloudflare reduce any additional latency added by processing the HTML file. If the feature is turned on, for any HTTP response with an HTML Content-Type, Cloudflare will parse all JavaScript script tag source attributes. If any are found linking to polyfill.io, Cloudflare will rewrite the src attribute to link to their mirror instead. Cloudflare map to the correct version of the polyfill service while the query string is left untouched. The logic will not activate, however, if a Content Security Policy (CSP) header is found in the response. This ensures we don’t replace the link while breaking the CSP policy and therefore potentially breaking the website.
‘’’
What is polyfill.io? It offers polyfills – bits of JavaScript code that automatically add functionality to older browsers that is found in newer versions. These in-fills make life easier for developers in that by using polyfillers, they know their web code will work across a greater range of browsers. Websites can load and run polyfill.io’s code every time someone visits one of their pages. This is obviously fine if the code is harmless, but if it turns harmful, that’ll result in sites executing someone else’s malicious code in visitors’ browsers without anyone immediately realizing it. That code could redirect people to bad places, spy on what they do on the page, and more.
‘’’
At the time this publishing, the pollyfill.io domain has been shut down!
@OfclyGoodenough @scamterminator2021 @MajorLeeAwesome @JusticeinTexas @Sol @Tillianne @CatMan @drwat @LordOfTheRings @Jhawk