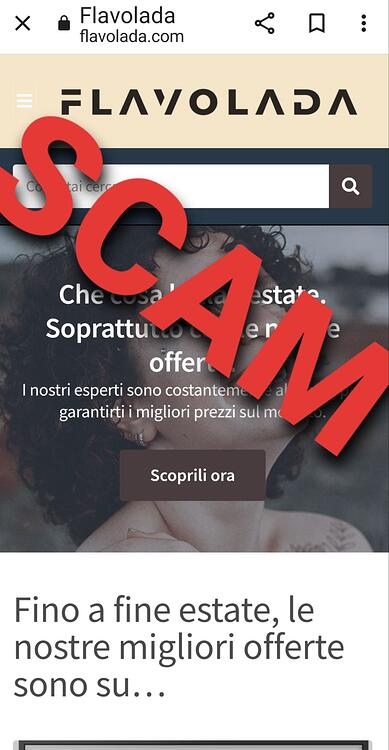
FakeShop;
Flavolada
The scam data bank:
IBAN: IT63X3253203200006571770739
Intestatario: Angela Cenci
BIC (SWIFT): SIGPITM1XXX
Courtesy of comsic-1337x
As always,
Enjoy the information <3
PORT STATE SERVICE VERSION
2053/tcp open ssl/http nginx
| ssl-cert: Subject: commonName=*.flavolada.com
| Subject Alternative Name: DNS:*.flavolada.com, DNS:flavolada.com
| Issuer: commonName=E1/organizationName=Let's Encrypt/countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA384
| Not valid before: 2022-07-26T08:54:35
| Not valid after: 2022-10-24T08:54:34
| MD5: 6672 d16a ad5d c617 06c8 2b92 f7a9 f1d7
|_SHA-1: dbc6 1ed9 4bf2 ddaa a5be eacb 75f5 14ad cb75 7fe6
|_http-server-header: cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
2082/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Did not follow redirect to https://flavolada.com/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
2083/tcp open ssl/http nginx
| ssl-cert: Subject: commonName=*.flavolada.com
| Subject Alternative Name: DNS:*.flavolada.com, DNS:flavolada.com
| Issuer: commonName=E1/organizationName=Let's Encrypt/countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA384
| Not valid before: 2022-07-26T08:54:35
| Not valid after: 2022-10-24T08:54:34
| MD5: 6672 d16a ad5d c617 06c8 2b92 f7a9 f1d7
|_SHA-1: dbc6 1ed9 4bf2 ddaa a5be eacb 75f5 14ad cb75 7fe6
|_http-server-header: cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
2086/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Did not follow redirect to https://flavolada.com/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
2087/tcp open ssl/http nginx
| ssl-cert: Subject: commonName=*.flavolada.com
| Subject Alternative Name: DNS:*.flavolada.com, DNS:flavolada.com
| Issuer: commonName=E1/organizationName=Let's Encrypt/countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA384
| Not valid before: 2022-07-26T08:54:35
| Not valid after: 2022-10-24T08:54:34
| MD5: 6672 d16a ad5d c617 06c8 2b92 f7a9 f1d7
|_SHA-1: dbc6 1ed9 4bf2 ddaa a5be eacb 75f5 14ad cb75 7fe6
|_http-server-header: cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
2096/tcp open ssl/http nginx
|_http-server-header: cloudflare
| ssl-cert: Subject: commonName=*.flavolada.com
| Subject Alternative Name: DNS:*.flavolada.com, DNS:flavolada.com
| Issuer: commonName=E1/organizationName=Let's Encrypt/countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA384
| Not valid before: 2022-07-26T08:54:35
| Not valid after: 2022-10-24T08:54:34
| MD5: 6672 d16a ad5d c617 06c8 2b92 f7a9 f1d7
|_SHA-1: dbc6 1ed9 4bf2 ddaa a5be eacb 75f5 14ad cb75 7fe6
|_http-title: 400 The plain HTTP request was sent to HTTPS port
8443/tcp open ssl/http Cloudflare http proxy
| ssl-cert: Subject: commonName=*.flavolada.com
| Subject Alternative Name: DNS:*.flavolada.com, DNS:flavolada.com
| Issuer: commonName=E1/organizationName=Let's Encrypt/countryName=US
| Public Key type: ec
| Public Key bits: 256
| Signature Algorithm: ecdsa-with-SHA384
| Not valid before: 2022-07-26T08:54:35
| Not valid after: 2022-10-24T08:54:34
| MD5: 6672 d16a ad5d c617 06c8 2b92 f7a9 f1d7
|_SHA-1: dbc6 1ed9 4bf2 ddaa a5be eacb 75f5 14ad cb75 7fe6
|_http-server-header: cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
8880/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Did not follow redirect to https://flavolada.com/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS`Preformatted text`
–
{
"host": "www.flavolada.com",
"ip": "104.21.23.178",
"port": "443",
"banner": "cloudflare",
"vulnerabilities": [
{
"id": "999957",
"OSVDB": "0",
"method": "GET",
"url": "/",
"msg": "The anti-clickjacking X-Frame-Options header is not present."
},
{
"id": "999100",
"OSVDB": "0",
"method": "GET",
"url": "/",
"msg": "Uncommon header 'alt-svc' found, with contents: h3=\":443\"; ma=86400, h3-29=\":443\"; ma=86400"
},
{
"id": "999970",
"OSVDB": "0",
"method": "GET",
"url": "/",
"msg": "The site uses SSL and the Strict-Transport-Security HTTP header is not defined."
},
{
"id": "999103",
"OSVDB": "0",
"method": "GET",
"url": "/",
"msg": "The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type."
},
{
"id": "999100",
"OSVDB": "0",
"method": "GET",
"url": "/index.php?",
"msg": "Uncommon header 'x-redirect-by' found, with contents: WordPress"
},
{
"id": "999997",
"OSVDB": "0",
"method": "GET",
"url": "/wp-admin/admin-ajax.php",
"msg": "Entry '/wp-admin/admin-ajax.php' in robots.txt returned a non-forbidden or redirect HTTP code (400)"
},
{
"id": "999996",
"OSVDB": "0",
"method": "GET",
"url": "/robots.txt",
"msg": "\"robots.txt\" contains 2 entries which should be manually viewed."
},
{
"id": "999966",
"OSVDB": "0",
"method": "GET",
"url": "/",
"msg": "The Content-Encoding header is set to \"deflate\" this may mean that the server is vulnerable to the BREACH attack."
}
]
}
–
---------
Searching at CVE (https://cve.mitre.org) for vulnerabilities...
-Last Reports:
+ CVE-2022-2225 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2225
+ CVE-2022-2147 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2147
+ CVE-2022-2145 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2145
+ CVE-2021-43800 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-43800
+ CVE-2021-3912 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3912
+ CVE-2021-3911 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3911
+ CVE-2021-3910 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3910
+ CVE-2021-3909 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3909
+ CVE-2021-3908 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3908
+ CVE-2021-3907 -> https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3907
---------
[Extra Info]
---------
Biggest File: https://www.flavolada.com/cdn-cgi/scripts/5c5dd728/cloudflare-static/email-decode.min.js
---------
–
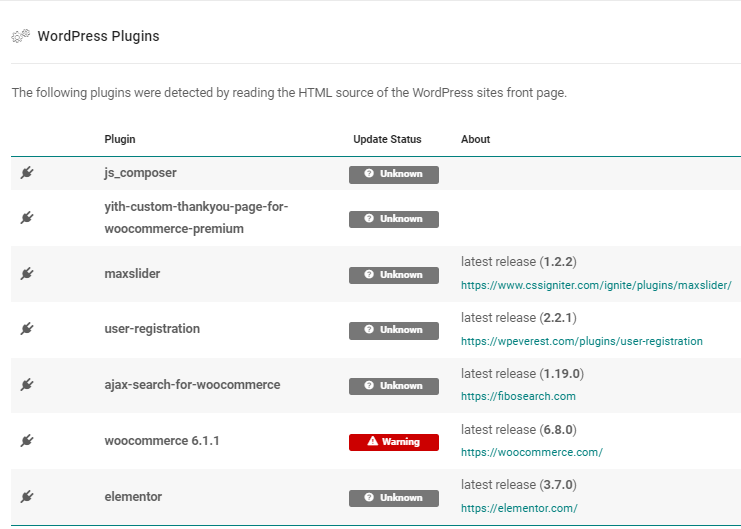
WordPress Version
- 6.0.1
Theme
- Nozama 1.9.3
2 WordPress Users:
- admin
- [detected but not enumerated]
–
SSL analysis:
---
* Certificates Information:
Hostname sent for SNI: flavolada.com
Number of certificates detected: 1
Certificate #0 ( _EllipticCurvePublicKey )
SHA1 Fingerprint: dbc61ed94bf2ddaaa5beeacb75f514adcb757fe6
Common Name: *.flavolada.com
Issuer: E1
Serial Number: 347145266269400426503927101099124089937872
Not Before: 2022-07-26
Not After: 2022-10-24
Public Key Algorithm: _EllipticCurvePublicKey
Signature Algorithm: sha384
Key Size: 256
Curve: secp256r1
DNS Subject Alternative Names: ['*.flavolada.com', 'flavolada.com']
Certificate #0 - Trust
Hostname Validation: OK - Certificate matches server hostname
Android CA Store (9.0.0_r9): OK - Certificate is trusted
Apple CA Store (iOS 13, iPadOS 13, macOS 10.15, watchOS 6, and tvOS 13):OK - Certificate is trusted
Java CA Store (jdk-13.0.2): OK - Certificate is trusted
Mozilla CA Store (2020-09-17): OK - Certificate is trusted
Windows CA Store (2020-10-01): OK - Certificate is trusted
Symantec 2018 Deprecation: OK - Not a Symantec-issued certificate
Received Chain: *.flavolada.com --> E1 --> ISRG Root X2 --> ISRG Root X1
Verified Chain: *.flavolada.com --> E1 --> ISRG Root X2 --> ISRG Root X1
Received Chain Contains Anchor: OK - Anchor certificate not sent
Received Chain Order: OK - Order is valid
Verified Chain contains SHA1: OK - No SHA1-signed certificate in the verified certificate chain
Certificate #0 - Extensions
OCSP Must-Staple: NOT SUPPORTED - Extension not found
Certificate Transparency: WARNING - Only 2 SCTs included but Google recommends 3 or more
Certificate #0 - OCSP Stapling
NOT SUPPORTED - Server did not send back an OCSP response
* TLS 1.2 Cipher suites:
Attempted to connect using 158 cipher suites.
The server accepted the following 7 cipher suites:
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 256 ECDH: x25519 (253 bits)
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 128 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 128 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
The group of cipher suites supported by the server has the following properties:
Forward Secrecy OK - Supported
Legacy RC4 Algorithm OK - Not Supported
The server has no preferred cipher suite.
* TLS 1.3 Cipher suites:
Attempted to connect using 5 cipher suites.
The server accepted the following 3 cipher suites:
TLS_CHACHA20_POLY1305_SHA256 256 ECDH: x25519 (253 bits)
TLS_AES_256_GCM_SHA384 256 ECDH: x25519 (253 bits)
TLS_AES_128_GCM_SHA256 128 ECDH: x25519 (253 bits)
The group of cipher suites supported by the server has the following properties:
Forward Secrecy OK - Supported
Legacy RC4 Algorithm OK - Not Supported
The server is configured to prefer the following cipher suite:
TLS_AES_256_GCM_SHA384 256 ECDH: x25519 (253 bits)
* SSL 3.0 Cipher suites:
Attempted to connect using 80 cipher suites; the server rejected all cipher suites.
* TLS 1.1 Cipher suites:
Attempted to connect using 80 cipher suites.
The server accepted the following 2 cipher suites:
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
The group of cipher suites supported by the server has the following properties:
Forward Secrecy OK - Supported
Legacy RC4 Algorithm OK - Not Supported
The server is configured to prefer the following cipher suite:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
* OpenSSL Heartbleed:
OK - Not vulnerable to Heartbleed
* TLS 1.0 Cipher suites:
Attempted to connect using 80 cipher suites.
The server accepted the following 2 cipher suites:
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
The group of cipher suites supported by the server has the following properties:
Forward Secrecy OK - Supported
Legacy RC4 Algorithm OK - Not Supported
The server is configured to prefer the following cipher suite:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
* SSL 2.0 Cipher suites:
Attempted to connect using 7 cipher suites; the server rejected all cipher suites.
–
I might have more fun, but this is enough funsies for now <3
lmao - anyway, enjoy ![]()
Hello there,
I’m going to take a look ![]()
Idem criminal gang;
Other scam data Bank:
IBAN: IT58I3253203200006571741134
Account: Sharon Ghidelli
BIC: SIGPITM1XXX