https://trhelp.top/
https://mgbhelp.top/
https://ppl.help9.top/
12/18/24 mzcare.help 188.114.96.3 Cloudflare/Namesilo - 40715
Same URL download
12/18/24 uwcare.help 188.114.97.3 Cloudflare/Namesilo - 23051
Same URL for download
| 12/18/24 | dcrcare.help | 78.40.117.18 | Alexhost/Namesilo - 10278 |
|---|---|---|---|
| 12/18/24 | sftre-tr.top | 37.221.64.49 | Alexhost/Namesilo |
hehelp.top
xuhelp.top
https://hehelp.top/
reversed their proxy
links back to
https://molatoriline.cyou/ -
37.221.65.128
here is some active codes
00066
00143
00236
00191
00227
00289
associated hosts
https://plphelp.top/
https://tgvhelp.top/
here is some notable information i collective from the connectwise sites you provided:
please reply or contact me in some way if you find a dynamic connectwise site loading the connectwise server(enter code page) once you visit it (so i can gather more information on the site)
https://ppl.help9.top/data.php?id=1|https://bortra0907.chelokipotleify.icu/guest|cloudflare
https://ppl.help9.top/data.php?id=5|https://pn3699.jigisekar.cyou/guest|176.123.1.201|pn6back63.site
https://ppl.help9.top/data.php?id=6|https://gajrokerist.cyou/guest|cloudflare
https://trhelp.top/data.php?id=1|https://molatoriup.cyou:8443/guest|offline
https://trhelp.top/data.php?id=2|https://gajrokeron.cyou:8443/guest|offline
https://trhelp.top/data.php?id=3|https://gajrokercast.icu:8443/guest|offline
https://trhelp.top/data.php?id=4|https://molatoriline.icu:8443/guest|offline
https://trhelp.top/data.php?id=6|https://cp3699.jigisekar.cyou/guest|offline
https://trhelp.top/data.php?id=7|https://cshelp.site/guest|offline
https://trhelp.top/data.php?id=8|https://cm0819.chelokipotleia.icu:8443/guest|cloudflare reversed:https://molatoriist.icu/guest|91.208.184.187|extra: cm369back6.site
https://trhelp.top/data.php?id=10|https://lf3699.jigisekar.cyou:8443/guest|offline
https://trhelp.top/data.php?id=11|https://bw4927.chelokipotleus.icu/guest|offline
https://trhelp.top/data.php?id=12|https://fn3699.kafinora.cyou/guest|offline
https://trhelp.top/data.php?id=13|https://qc3699.kafinora.cyou/guest|94.103.188.29|qc96back6.site
notice the similarity between cm369back6.site,pn6back63.site,qc96back6.site
in fact, there can be a regex-“^[a-z]{2}\d+back\d+\.site$”-to identify similar sites like this:
if someone actively observes recent registered domains then they should look out for sites similar to the ones seen above.
mentioning these sites before they are fully set up can help us identify connectwise servers that may go unnoticed
we can probably guess what https://fn3699.kafinora.cyou/guest used to be based on the information collected from https://qc3699.kafinora.cyou/guest
the result: fn96back6.site
hope this helps link past scam sites or future
note: not sure if these sites are active but i know they are online and are associated in some way with scamming people
https://eopcare.help/ ive reversed the cloudflare proxy back to https://elioua5.top/
https://hrhcare.live/
their connect wise site is obrm-h4.top|37.221.64.118
here is some active codes
00126
00078
00063
00198
00250
00271
00306
00307
00391
00399
00405
00408
00432
00469
00497
00523
00556
00572
gajrokerist.cyou seems to be associated with molatoriby.cyou
perfect! another dynamic site-https://securemyaccount.top
https://securemyaccount.top/data.php?id=1|https://bortra0907.chelokipotleify.icu/guest|cloudflare
https://securemyaccount.top/data.php?id=2|https://tshelp.site/|offline
https://securemyaccount.top/data.php?id=3|https://mcthelp.site/guest|offline
https://securemyaccount.top/data.php?id=4|https://qc3699.gropler.loginlink2.org/guest|offline
https://securemyaccount.top/data.php?id=5|https://pn3699.jigisekar.cyou/guest|176.123.1.20|pn6back63.site
https://securemyaccount.top/data.php?id=6|https://gajrokerist.cyou/guest|cloudflare
the sites seem to have almost the exact same structure as the one i previously posted about
looks like we can tie this paypal domain back to the others
McAfee
using cwcare.help
I can now safely confirm that these recent *care.help domains you have posted recently are all tied to one call center operating multiple scams-PayPal malware crypto Apple & Microsoft support and a bunch of tech support scams.
Good work on what you have found.
I might post further details on it once I decide what I’m doing with it
Hey @pertobe , I found something similar I think (it’s from my post on tsu but I’ll copy some here as well)
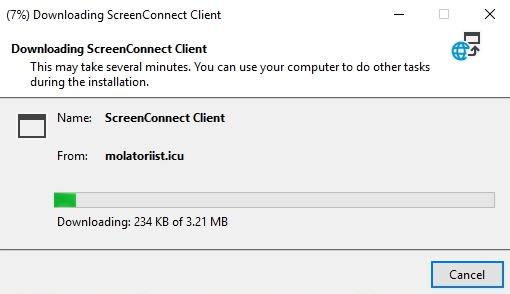
While downloading another CW installer via https://trhelp.top/ (12345 worked there) I saw this:
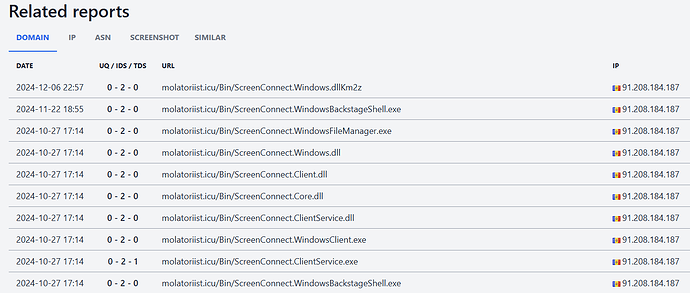
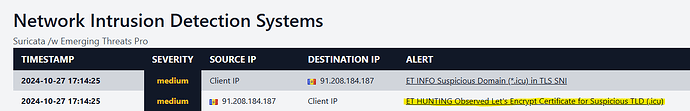
so I looked up molatoriist.icu and found these reports:
https://urlquery.net/report/298ef1bb-ee9f-4132-8667-51021bca4edb
https://urlquery.net/report/d38cdf7e-bee7-4579-9c99-022e2de21c80
![]()
the files in this report match the downloaded ScreenConnect installer folder later found in: C:\Users\XXX\AppData\Local\Apps.… (so I assume they are all hosted there)
I think they are reported on that site for some kind of certificate (maybe the digital signatures)
interesting, under related reports/screenshot there’s another .top site (maybe fetching the files from molatoriist.icu as well), I tried some of the others they look similar
My (simple) summary of the CW/SC game is:
- go to a .top site
- enter code and download the installer from there (installer includes the code for them to connect)
- by installing it grabs the rest of the exe/dll files from sites like molatoriist.icu
If that’s correct is it helpful to report molatoriist.icu as well? (no clue how and which reason to use). The registrar for trhelp.top and molatoriist.icu is Gname.com Pte. Ltd.
It has also helped me uncover 100s of different scam operations running currently that I will be taking action against and uploading an update in the future about it